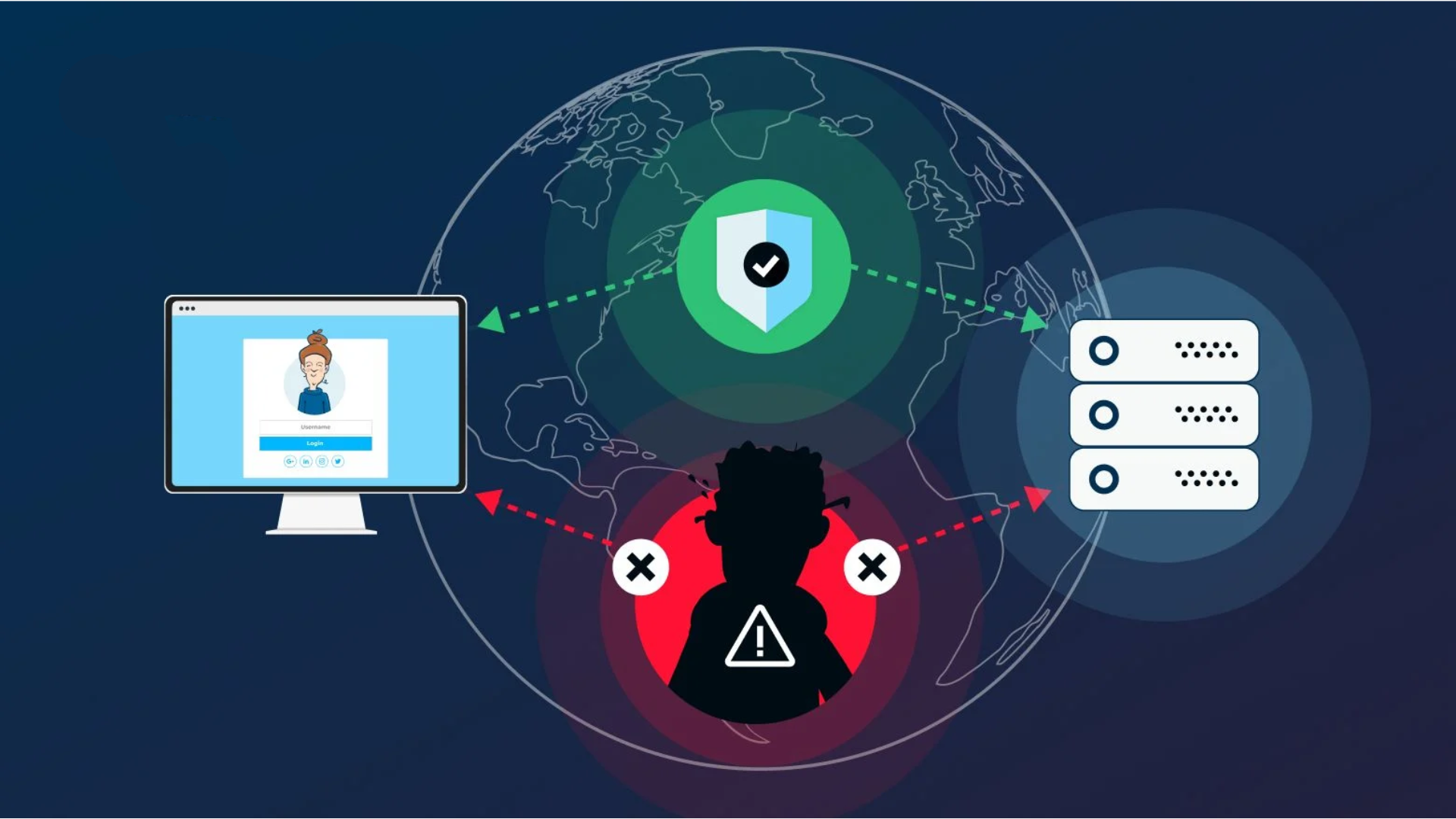
What is a man-in-the-middle attack on DNS?
The internet is something we use every day without thinking about how it works. When you type a website’s name into your browser, your computer finds the right website by using a system called DNS (Domain Name System). But sometimes, hackers can trick this system to send you to a fake website. This is called a Man-in-the-Middle (MITM) attack on DNS.
In this article, I’ll explain what this attack is, how it works, and how you can protect yourself from it in a way that is easy to understand.
What is a DNS Man-in-the-Middle Attack?
A Man-in-the-Middle attack on DNS happens when a hacker intercepts your internet request and redirects you to a fake website. This can be dangerous because you might enter personal details, like passwords or credit card numbers, without knowing that the website is fake.
To understand this better, let’s look at how DNS normally works.
How DNS Works
- You type a website’s name (e.g.,
www.bank.com) into your browser. - Your computer asks a DNS server for the IP address of that website.
- The DNS server finds the correct IP address and sends it back.
- Your browser loads the website.
Now, in a Man-in-the-Middle attack, a hacker changes this process to trick you.
How Does a DNS MITM Attack Work?
A hacker can take control of your internet traffic in different ways. Here are the most common methods:
1. Fake DNS Server
- The hacker sets up a fake DNS server that sends the wrong IP address when you try to visit a website.
- This can happen if your network is not secure or if your router has weak settings.
2. Spoofing DNS Responses
- The hacker sends fake responses to your computer before the real DNS server can reply.
- Your computer believes the fake response and loads the wrong website.
3. Public Wi-Fi Attacks
- If you use public Wi-Fi, a hacker can act as the network owner.
- They can see what websites you visit and redirect you to fake sites.
4. Malware on Your Device
- Some viruses or malware can change your computer’s DNS settings.
- This forces your browser to visit the hacker’s website instead of the real one.
What Can Hackers Do with This Attack?
If a hacker successfully performs a Man-in-the-Middle attack on DNS, they can:
✅ Steal your usernames and passwords.
✅ Trick you into entering credit card details.
✅ Install malware on your computer.
✅ Show fake versions of websites (like banking sites).
✅ Track your online activity.
This is why it’s important to protect yourself.
How to Protect Yourself from DNS MITM Attacks
There are several simple steps you can take to stay safe from these attacks.
1. Use Secure DNS Services
Instead of using your internet provider’s DNS, you can use trusted DNS services like:
- Google Public DNS (
8.8.8.8,8.8.4.4) - Cloudflare DNS (
1.1.1.1) - OpenDNS (
208.67.222.222,208.67.220.220)
These are more secure and can help protect you from attacks.
2. Avoid Public Wi-Fi for Sensitive Activities
If you must use public Wi-Fi, avoid logging into your bank account or making online purchases. Hackers can easily intercept your data on unsecured networks.
3. Enable HTTPS Everywhere
Always check if a website uses HTTPS instead of HTTP. Websites with HTTPS are encrypted, making it harder for hackers to intercept your data.
4. Keep Your Router Secure
- Change the default password on your router.
- Update your router’s firmware regularly.
- Disable remote access to your router if you don’t need it.
5. Use a VPN (Virtual Private Network)
A VPN encrypts your internet traffic, making it much harder for hackers to intercept your DNS requests.
6. Scan Your Device for Malware
Run a virus scan regularly to check for malware that might be changing your DNS settings.
Conclusion
A Man-in-the-Middle attack on DNS is a serious security threat, but it’s not difficult to protect yourself. By using a secure DNS, avoiding risky Wi-Fi networks, and keeping your devices updated, you can stay safe online.